- Baseline and improve security posture
- Realtime reports for data driven decisions
- Security posture quantify, validate assumptions
- Leading Trusted Community Circle and R&D Team
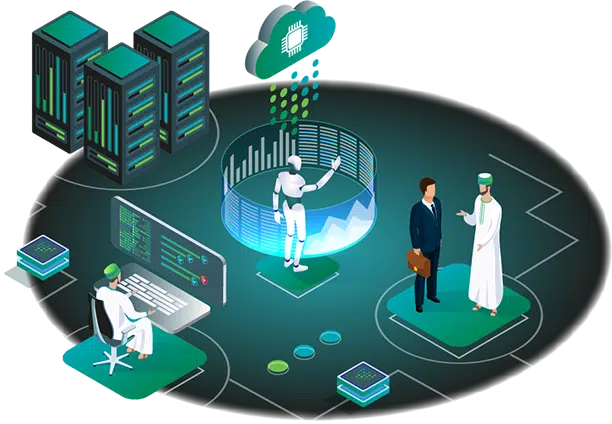
Cyber Security Drill Test Test Your Cybersecurity Regularly and Save up to $1.2 Million by Shortening Data Breach Life Cycles.
Test Your Systems with a Cybersecurity Drill Test by Oman Data Park

“No battle plan survives contact with the enemy.” This quote from the military applies perfectly to cybersecurity. If your systems are not tested, then you cannot know if they will work.
We can help you test your systems and prepare responses. During a cybersecurity drill test, we will deploy lightweight agents to probe your cybersecurity defenses.
These probes will include:
- Challenges to your security postures
- False phishing and ransomware attacks
- Validation scenarios to test network policies
- Preconfigured attack scenarios designed from real cases
- Various actors such as insider threats and national attacks
Following this test, a clear executive report will be delivered to your company. Action items can be used to enhance your security perimeter and build your company’s culture of cyber hygiene.
Preparing for an attack and testing your systems will help your company raise its security to the highest possible level.
Key Benefits
- Attack scenario testing for end- to-end security process workflows
- Validation scenarios to verify point-product effectiveness and ROI
- Compare current security posture against historical baselines
- Continuous automated testing as your network changes and evolves
- Integrations in to major SIEM technologies and log management tools to measure detection and prevention effectiveness
- Measure and validate detection and prevention capabilities
- Provide a methodology for selection of security technologies
- Quantify and reduce business risk
- Immediate evaluation of security readiness
- Maximize the effectiveness of security infrastructure
- Prioritize resource allocation
- Identify security gaps and blind spots
- Improve the maturity of your security program
- Create a data driven security lifecycle.
Features
Scenario repository
Attack scenarios – Stages
- Persistence
- Privilege Escalation
- Lateral Movement
- Access to Data Stores
- Command and Control
- Data Exfiltration
Attack scenarios – Threat actors
- National Actors
- Insider Threats
- Cyber Criminals
Validation scenarios – Technology Testing
- Access/Routing/Availability
- Data Loss Prevention (DLP)
- Content/Web Filtering
- Firewall
- Network and Host IPS/IDS
- AntiVirus (AV)
- SIEM
- SSL Certificates
- Executive reporting
- Lightweight agents
- Critical security metrics
- Intuitive management
- Active user community
- Knowledge base of scenarios and mitigations
- Project templates with smart defaults
Data Breaches Can Linger for 314 Days or Longer

The average life cycle of a data breach is 314 days. From the moment a criminal breaches your systems until the damage is repaired, your business is exposed and could be losing money.
In an interview with imeetcentral, Chris Covell, CIO with Absolute Software said “Having crisis communications plans in place for media, customers, partners, and shareholders will enable a fast, efficient response.” He added, “This includes creating draft email communications, press releases, and landing pages to explain what happened, how your company is addressing it, and what customers should do in the meantime.”
Despite the risks of a breach and the rewards of a plan, most businesses are unprepared. IBM discovered 77% of security and IT personnel do not believe their business has a cybersecurity incident response plan that is applied consistently throughout the company.
Are the risks really so high? Here are a few alarming statistics:
- 53% of companies have over 1,000 sensitive files accessible to every employee.
- 38% of all users have a password that never expires.
- 24% of data breaches are caused by human error.
A cyberattack occurs every 39 seconds.
Is your business prepared?
Test Your Security to Save $1.2 Million

A cybersecurity drill test will reveal vulnerabilities in your system and help your business prepare a rapid response to any penetration.
This could save your business $1.2 million. Companies who contain a breach and repair the damage in less than 200 days save this amount compared to companies that respond slower.
The losses incurred during a breach are from a few different sources:
- The attackers may demand a ransom for returning the data. Ransom demands may happen repeatedly.
- Government organizations can fine businesses for inadequate security preparations.
- Customers may sue the company and these lawsuits can be awfully expensive.
- Revenue will drop because customers leave businesses that expose their personal data.
An untested system and a poor response could cost your company millions of dollars. There is no greater existential threat to your business.